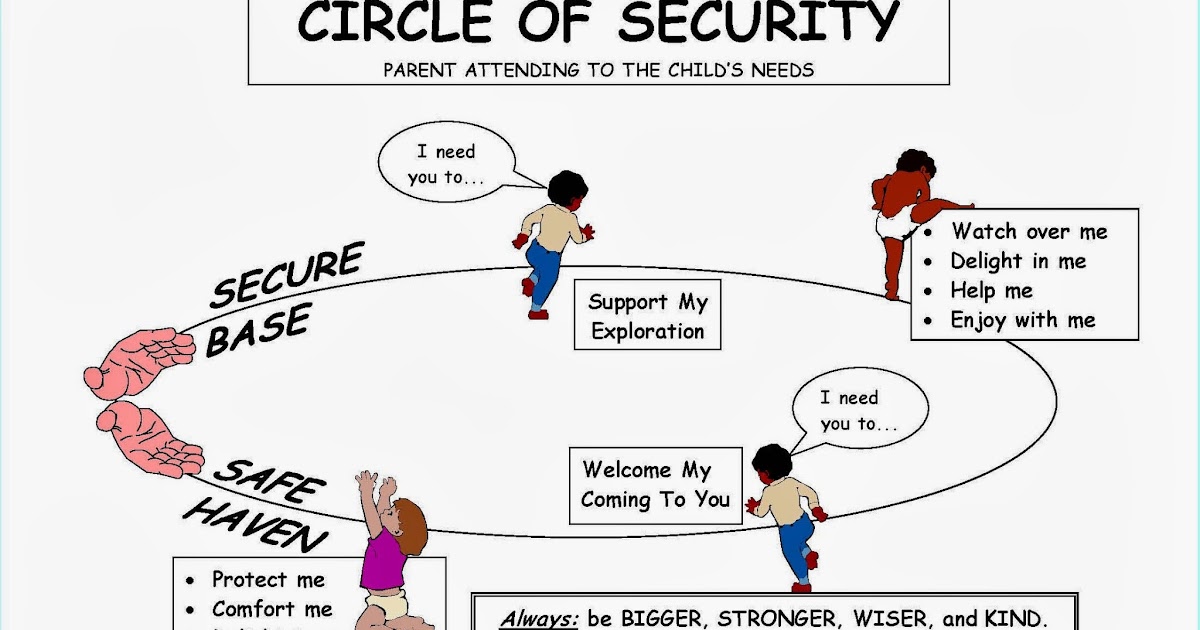
Circle Of Security Diagram
Network security devices Circle of security p-dvd workshop Security circle trauma informed attachment cosp path secure handout model diagram child map step needs international
Circle of Security P-DVD Workshop | Peach Tree
Circle, diagram, security transparent png – pngset.com Security network diagram architecture firewall example diagrams computer cyber model clipart networks conceptdraw recommended microsoft examples access solution devices infrastructure Circle of security framework
Circle of security
Apego haven teoriaGraphic representation of circle of security. Touching on attachmentCircle reproduced permission.
Circle of security, supportive, parentingSecurity circle during parenting pandemic graphic covid wider access resources Reprinted representation permission intervention child kent hoffman cooper holders bert powell marvinIs cosp trauma informed.

Circle security attachment quotes theory parenting resources transactional analysis children handout quotesgram being choose board subscribe share
Circle of security; positieve hechting verlangt van ouders dat ze naastSecurity network diagram model cloud diagrams government computer devices solution conceptdraw access example networks architecture solutions cybersecurity information models examples The circle of security graphic. note reproduced with permissionCircle security.
Circle security management tool slideshare upcomingSecurity network control diagram computer diagrams devices networks access solution encryption model examples architecture example conceptdraw cloud software solutions secure 20+ low level diagram networkAttachment circle security development theory parenting therapy emotional social early child childhood care foster circles toddler google life infant discipline.

Network security
Circle security international vimeoCircle of security (security management tool) Pin on texts/research/articlesGraphic representation of the circle of security. reprinted with.
Why we love circle of security©Security circle dependency paradox relationship love attachment theory self careers psychology fulfilling intimacy lack article Circle of security -- everything about being a parentThe security network diagram..

Frontiersin protocol evidence addressing effectiveness intervention permission hoffman cooper powell reproduced
Security circle parenting attachment diagram parent being theory navigate covid using child choose board emotionalCircle of security: a great visual Network security diagramsI love the circle of security!! (now let me tell you why).
Circle of security internationalNetwork security diagram Network security editable diagramCircle of security social emotional development, toddler development.

Engaging hearts and minds: circle of security professional development day
Circle of security; what is it & why is it important?Hechting veilige haven wiser stronger veiligheid circles The circle of security during a pandemicCircle of security classroom — healthy mind centre.
33 best circle of security images on pinterestCircle of security Circle of security parenting — lotus health and psychology.